OAuth2 typ with LinkedIn
Let’s dive into the step-by-step process of setting up OAuth authorization in Integray using LinkedIn login.
LinkedIn Setup
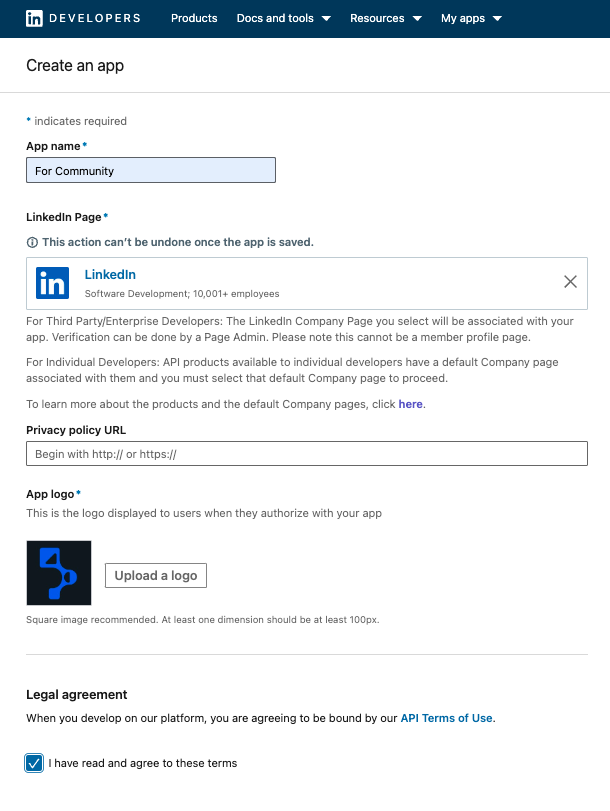
The first step is to create your own "app" on the LinkedIn site: Create a LinkedIn app. This will provide the key information needed for authorization.
For the new application, you’ll need to fill out the following:
- App name
- LinkedIn Page (you can add a general page, no verification is required)
- Upload logo
- Agree to the terms by checking the checkbox
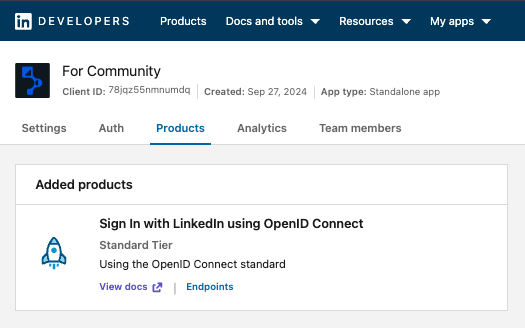
Once completed, click Save. Next, add a product (for example, one shown in the screenshot) and agree to the terms and conditions.
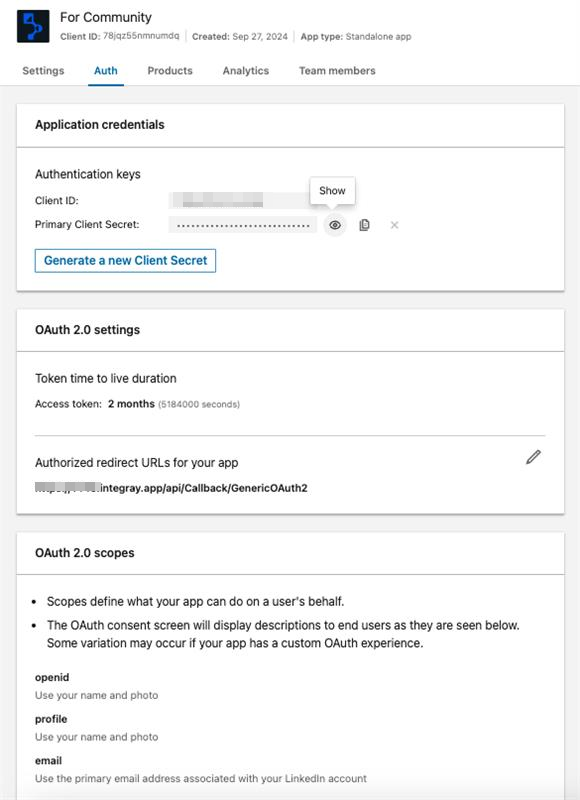
In the Auth tab, you will find the Client ID and Client Secret, fill in the Redirect URL, and determine the appropriate Scope (make sure to refresh the page if you don't see available scopes). Further steps for configuring the Redirect URL will be provided below.
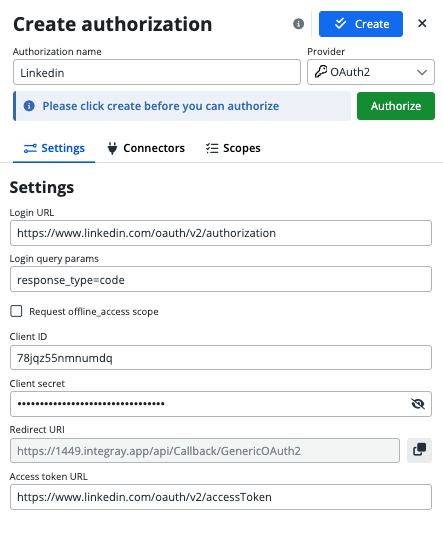
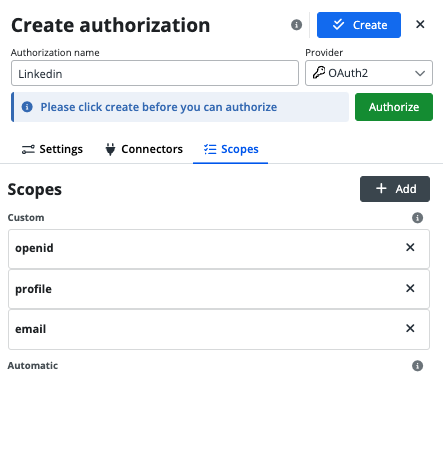
Now, let's move over to Integray. In the new Authorizations section, we’ll create a new authorization by clicking +Add and selecting OAuth2 as the provider. More about Authorizations feature on our Learn
Integray Authorization Settings
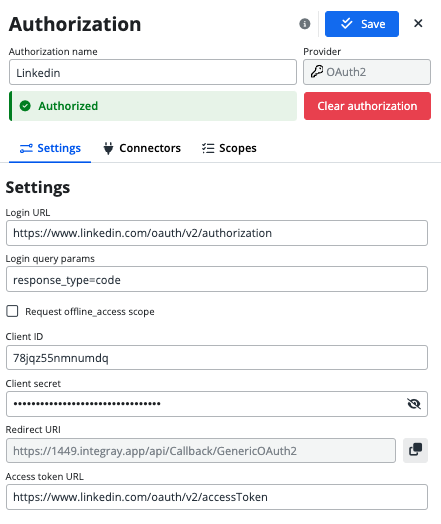
- Login URL: for LinkedIn it is
https://www.linkedin.com/oauth/v2/authorization - Login query params: use the pre-filled settings
response_type=code - Request offline_access scope: LinkedIn does not support this scope, so we will mark the checkbox as
False - Client ID: use the information from the Auth tab on the LinkedIn Developer site.
- Client Secret: use the information from the Auth tab on the LinkedIn Developer site.
- Redirect URI: predefined to the endpoint
api/Callback/GenericOAuth2 - Access Token URL: for LinkedIn it is
https://www.linkedin.com/oauth/v2/accessToken
Configuring connectors
Currently, it is recommended to use this authorization with the Advanced Rest API Connector.
For more details and specifications of endpoints, you can refer to the documentation in the Endpoints tab for the selected product, and for more detailed documentation, check the View docs tab.
Reviewing and Customizing Scopes
In the Scopes tab, you must define custom scopes to specify permissions according to your company’s needs, adhering to the principle of least privilege for enhanced security.
As we saw in the Auth tab on LinkedIn for developers, Scopes are defined based on the product you choose for your app. In Integray, we need to input the same scopes; otherwise, the authorization will not work correctly.
Once connectors and scopes are configured, the authorization setup is complete. The system is ready for secure interactions, click the Authorize button. This action will redirect you to the provider’s login page, where you will enter your credentials to sign in.
During the login process, you must approve the User consent screen, which is a dialog or webpage presented by the authorization server. This screen informs you about the specific permissions or Scopes the application requests access to. You must review these permissions and provide your consent to allow the application to access your data within the specified scope.
After successful authentication, the status indicator will change from Not authorized to Authorized, confirming the authorization.
Finally, click the Save button to store the new authorization.
Thanks for reading, and I hope this guide helps you with your setup!
Step-by-Step OAuth2 Authorization Process Using Microsoft Azure on the YouTube.
Other useful Links: