Reservanto
When you use authorization with a predefined provider in Integray, such as Reservanto, the setup process is efficient and straightforward due to the pre-configured settings.
Settings
In the first tab, Settings, you will find that this section is empty, as all essential details, including Client ID, Secret key, and Callback URL are automatically configured. This eliminates the need for manual setup, as Integray has automated these configurations to align with the provider’s requirements. This setup ensures secure communication and proper authorization flows between Integray and the provider’s services.
Configuring connectors
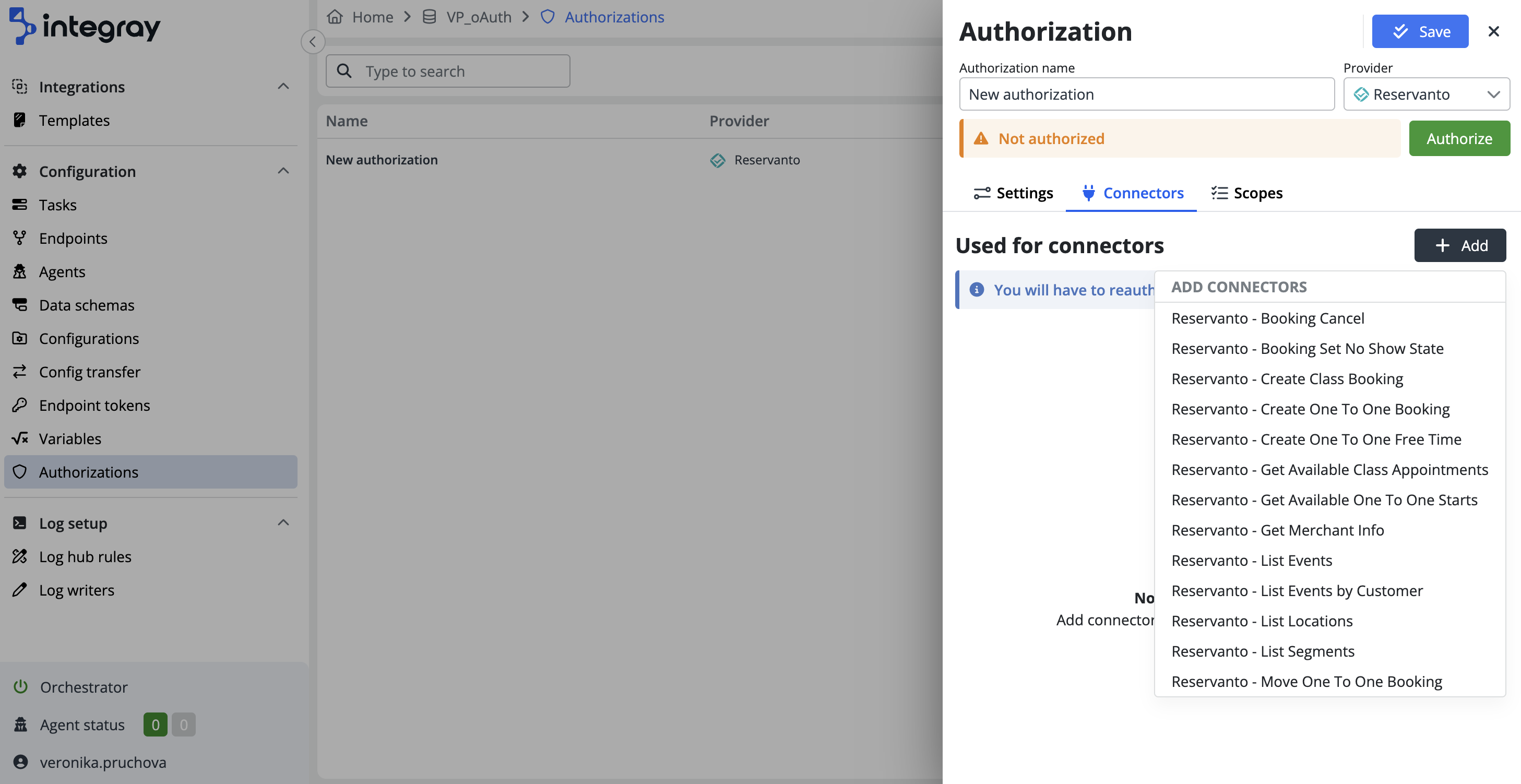
Move to the Connectors tab, where you can select the desired connector from the dropdown menu. This step links the authorization to specific services, with the system automatically handling the integration using the predefined settings, ensuring a seamless setup.
Based on the selected services, the system also automatically pre-fills the appropriate scopes, defining the necessary permissions for the connector’s operation.
Note
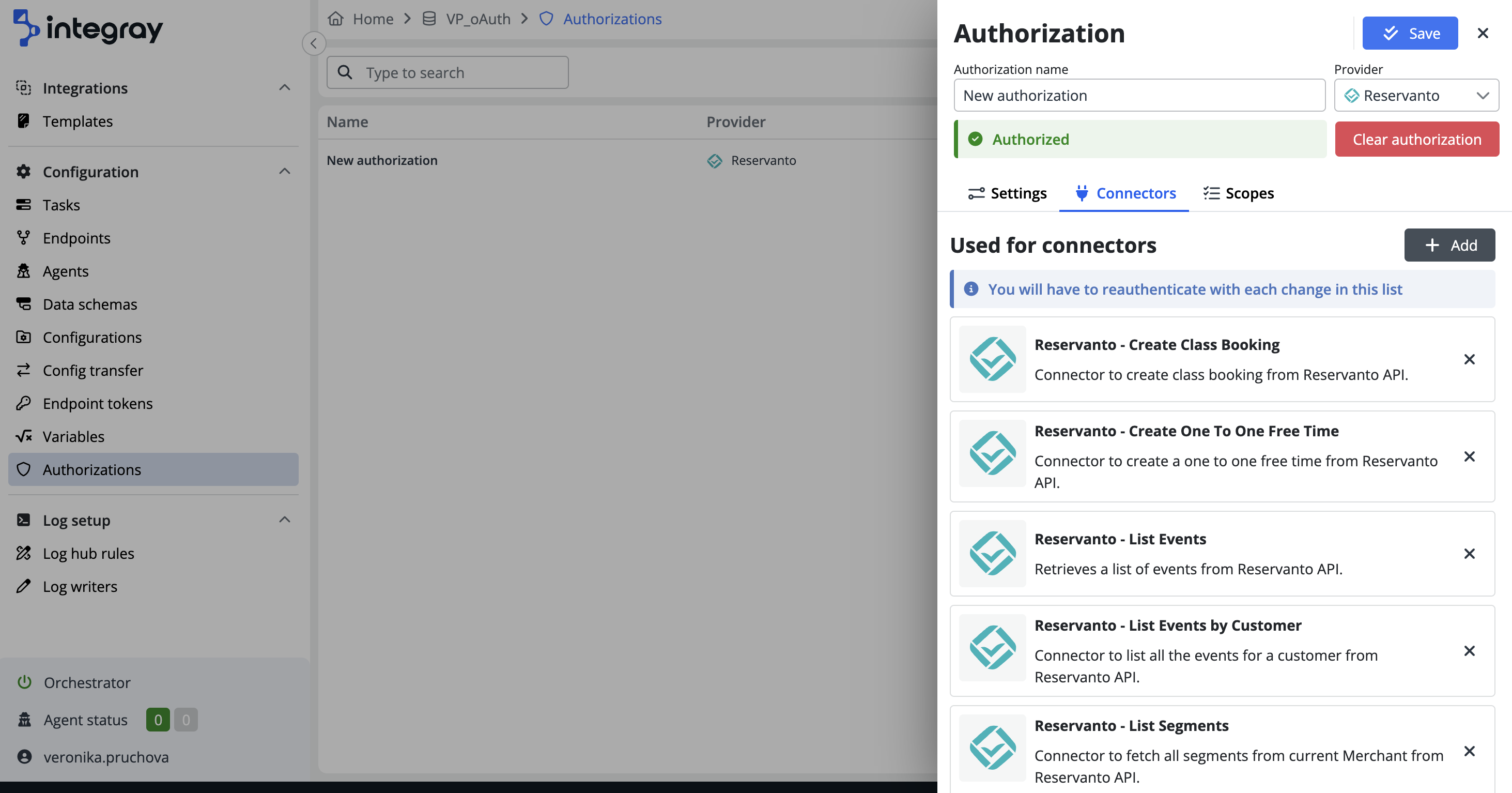
Under a single authorization, you can associate multiple connectors from the same provider.
Reviewing and Customizing scopes
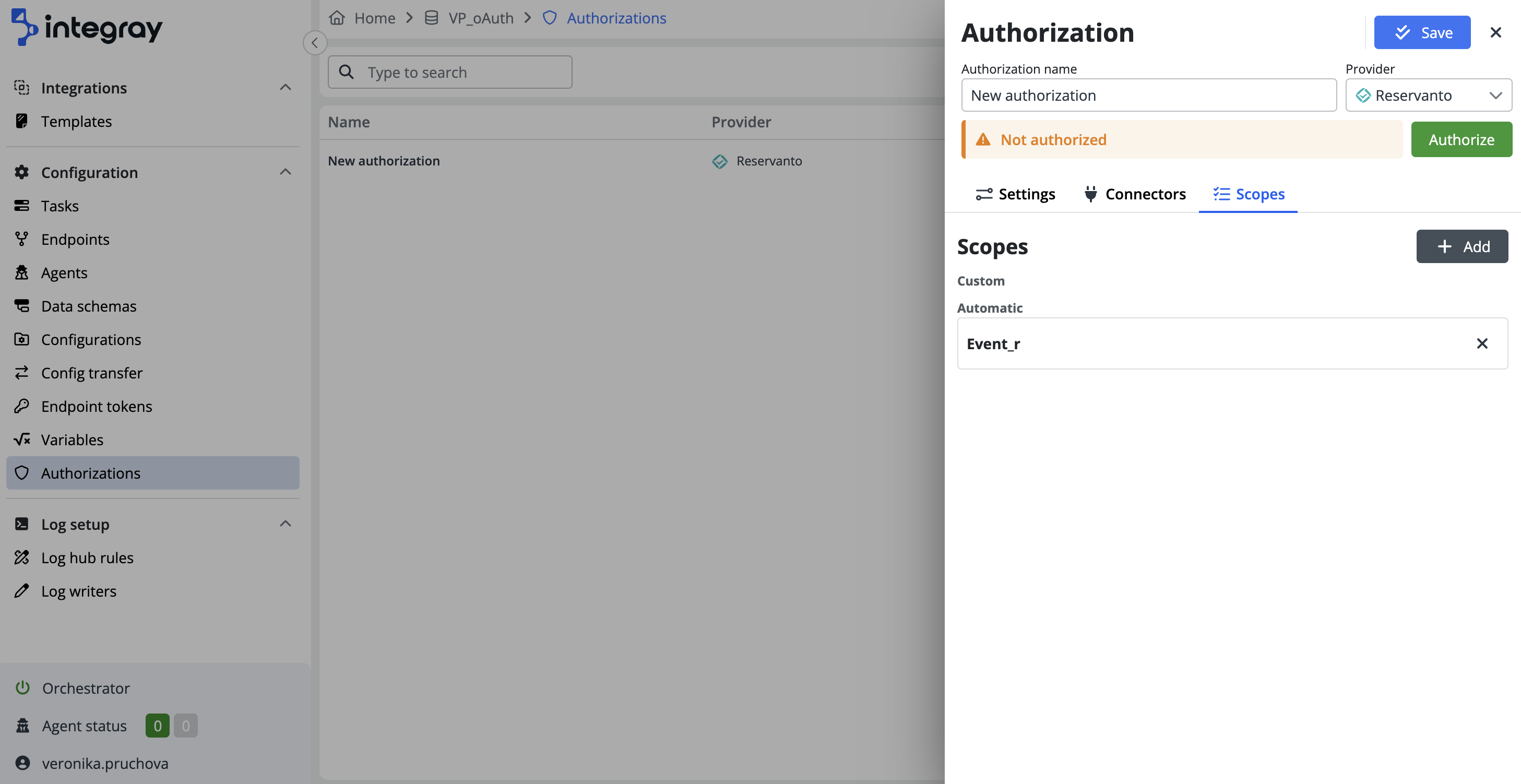
In the Scopes tab, Integray automatically adds necessary scopes, defining the access level for the connector.
These automatic scopes are automatically pre-filled based on the selected services, ensuring that the appropriate permissions are in place for the connector’s operation. Additionally, you can define custom scopes to specify permissions according to your application’s needs, adhering to the principle of least privilege for enhanced security. For more about Scopes see article here.
Once connectors and scopes are configured, the authorization setup is complete. The system is ready for secure interactions, click the Authorize button. This action will redirect you to the provider’s login page, where you will enter your credentials to sign in.
Risks of using a personal account for authorization
If the authorization uses a user’s own account credentials and that account is deactivated, the authorization will be canceled, and the integration will stop working.
During the login process, you must approve the User consent screen, which is a dialog or webpage presented to you by the authorization server. This screen informs you about the specific permissions or Scopes the application requests access to. You must review these permissions and provide their consent to allow the application to access their data within the specified scope.
After successful authentication, the status indicator will change from Not authorized to Authorized, confirming the authorization.
Finally, click the Save button to store the new authorization.
Publish needed
After authorizing or deauthorizing, it’s necessary to publish these new changes to the cache.