Tokens
Tokens serve as a means of securing specific endpoints. By assigning tokens to individual endpoints, you can meticulously safeguard your environment. This section facilitates the administration of both primary and secondary tokens.
If the Authentication type is set to Token on the General tab in the Security section, the additional tab Tokens is available.
On the Tokens tab you can configure POST, GET, PUT, PATCH and DELETE primary tokens or select secondary tokens from the provided menu.
Towards the bottom of the screen, use the Hide unassigned toggle to conceal secondary tokens that the user hasn't assigned to the endpoint.
Note: generated tokens are primary tokens and it is not recommended to use those externally. Recommendation is to use secondary tokens generated in the Endpoint tokens and mapped to the primary tokens. There may be more secondary tokens mapped to one primary. Advantage of this option is possibility to assign different tokens to different e.g. applications. This provides the opportunity on the Endpoint data viewer to see what applications are communicating via the endpoint. Additionally, if there is a need to switch off the integration branch with specific application, then switching off the mapping to secondary token will serve the purpose without affecting any other integration branches linked to the same endpoint.
POST, GET, PUT, PATCH and DELETE primary tokens are generated automatically when the General > Authenitication > Token is active.
Generate button can be used to re-generate the primary token. Copy button can be used to copy the token to clipboard.
Endpoint tokens
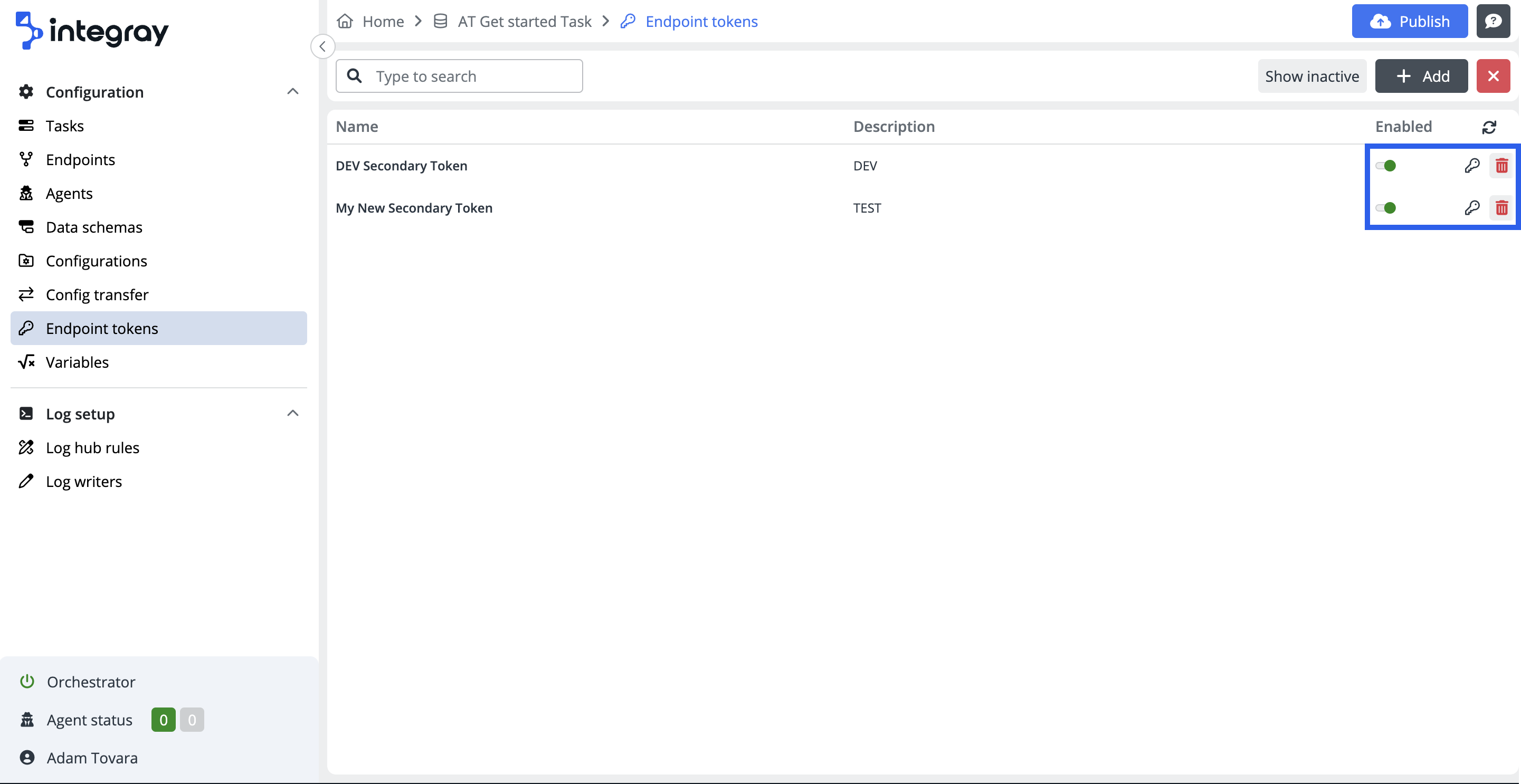
The item on the content navigation menu Endpoint tokens navigates the user to the Endpoint token list, where all the configured secondary endpoint tokens are listed. Default view displays the active tokens only.
The endpoint list view provides the user with essential information about the endpoint tokens:
Name and Description. It is recommended to utilize the secondary tokens per application and use the name of the application when naming the token. This is very useful when consequently viewing data on the Endpoint data viewer and using filter Tokens. This way, it is possible to practically display integratioins with specific application.
The endpoint tokens line contains three more controls:
-
Enabled toggle - the control to enable or disable the selected secondary token. Please refer to the text about tokens above to understand better how to use it to activelly manage integrations.
-
Deactivate token / Activate token - these icons dynamically adapt based on whether active or inactive tokens are currently displayed.
-
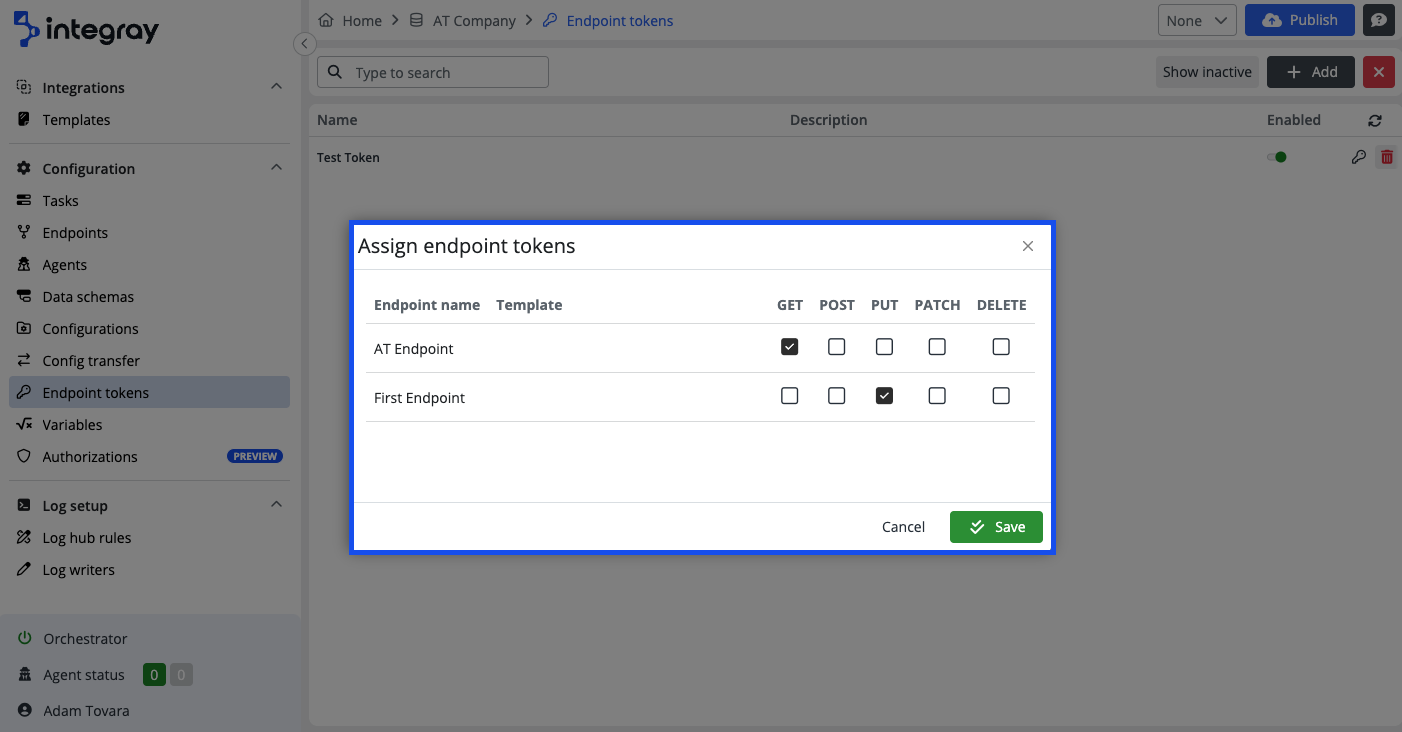
Assign endpoint tokens - click the button to open the Assign endpoint tokens modal dialog window. Within this modal, you can assign a secondary token to a specific endpoint.
Create a new Endpoint token
Click the +Add button to open the modal dialog window Token settings
-
Name - Define the name of the token following above mentioned recommendation.
-
Token - Randomly generated set of 64 alphanumeric characters.
-
Click the eye icon to reveal or hide the token.
-
Click the rotate arrow button to generate or re-generate the token value. Please mind each click on the button regenerates the value again.
-
Click the copy button to copy the value of the token.
-
-
Description - Additional option for token use description.
-
Enabled toggle enables or disables the configured token settings.